Wsb-Detect – Tool To Detect If You Are Running In Windows Sandbox (

wsb-detect allows you to detect if you are running in Home windows Sandbox (“WSB”). The sandbox is used by Windows Defender for dynamic examination, and usually manually by security analysts and alike. At the tail end of 2019, Microsoft introduced a new aspect named Windows Sandbox (WSB for quick). The methods applied to fingerprint WSB are outlined under, in the techniques portion. Really feel cost-free to submit a pull request if you have any fingerprinting tips. I’ve been messing about with it now and then, I will have extra on Windows Sandbox coming shortly.
Home windows Sandbox lets you to speedily, in just 15s, create a disposable Hyper-V based Virtual Machine with all of the features a familiar VM would have these as clipboard sharing, mapping directories etcetera. The sandbox is also the underlay for Microsoft Defender Software Guard (WDAG), for dynamic assessment on Hyper-V enabled hosts and can be enabled on any Home windows 10 Pro or Company device. It truly is not particularly interesting, but nevertheless could demonstrate beneficial in implant growth. Thank you to my friend Jonas L for direction when I was exploring the sandbox internals (much more to appear on this).
Utilization
The detect.h header exports all of the capabilities which can be merged to detect if
#include things like
#incorporate "detect.h"
int key(int argc, char** argv)
wsb_detect_username())
places("We are in Home windows Sandbox!")
return
return 1
Strategies
wsb_detect_time
The impression for the sandbox appears to be built on Saturday, December 7, 2019, 9:14:52 AM – this is all over the time Windows Sandbox was launched to the public. This examine cross references the creation timestamp on the mountmgr driver.
wsb_detect_username
This process will check if the existing username is WDAGUtilityUserAccount, the account employed by default in the sandbox.
wsb_detect_suffix
This strategy will use GetAdaptersAddresses, wander above the checklist of adapters, and compare the DNS suffix to mshome.web – which is utilized by default in the sandbox.
wsb_detect_dev
Checks if the raw unit .GLOBALROOTdevicevmsmb can be opened, which is employed for conversation with the host more than SMB.
wsb_detect_cmd
On startup, search underneath the RunOnce crucial in HKEY_Neighborhood_Device for a command which sets the password in no way to expire.
wsb_detect_office environment
Checks for the OfficePackagesForWDAG in the current root drive, which seems to be employed for Windows Defender Microsoft Business emulation.
wsb_detect_proc
Checks for CExecSvc.exe, which is the container execution support, dealing with a large amount of the major lifting.
wsb_detect_genuine
A extra generic strategy when it arrives to sandbox detection, having said that from tests the Windows will not appear to be verified as legit in the VMs
Trivia
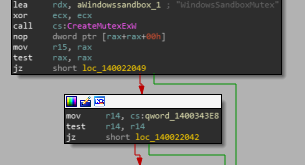
If you would like to call me more rapidly, really feel free to get in touch with me on Twitter or e-mail. Also, it really is probable on the host to detect if the sandbox is functioning, by examining if you can build a mutex named WindowsSandboxMutex. This limits the sandbox to 1 digital-device for every host, even so, you can launch this mutex by only duplicating the manage and calling ReleaseMutex – viola, you can have a number of situations.