Winshark – Wireshark plugin to work with Event Tracing for Windows

Wireshark plugin to perform with Occasion Tracing for Windows
Microsoft Concept Analyzer is getting retired and its down load deals were eradicated from microsoft.com sites on November 25, 2019. Wireshark has developed a substantial library of network protocol dissectors. The greatest software for Windows would be just one that can get and blend all sorts of logs…
Welcome Winshark!!!
Winshark is based on a libpcap backend to capture ETW (Function tracing for Windows), and a generator that will create all dissectors for recognised ETW providers on your equipment. We’ve added Tracelogging support to protect nearly all log tactics on the Home windows Operating Process.
With Winshark and the energy of Home windows, we can now capture Community and Event Logs in the exact same resource. Windows exposes a large amount of ETW suppliers, in distinct a single for community seize -) No extra have to have for an external NDIS driver.
This is a substantial improvement in phrases of use:
- Allow to combine all variety of functions (technique and community)
- Allow to use of Wireshark filtering on party log
- Help to observe network and technique logs by System ID!!!
- Permit to capture Home windows log and community trace into a unique pcap file!!!
- Seize NamedPipe via NpEtw file procedure filter driver
If you want to:
Set up
You should set up Wireshark just before. Then just set up Winshark.
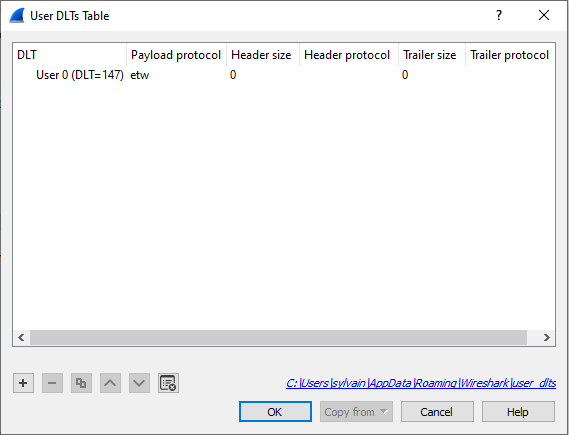
At present, you have to question Wireshark to interpret the DLT_Consumer 147 as ETW. This is because you have not yet a true price from libpcap for our new Details Backlink. We issued a pull request to have a dedicated DLT benefit it is continue to pending. To do that you have to open up Tastes tab less than the Edit panel. Decide on DLT_Person beneath Protocols and Edit the encapsulations desk:
And set etw for DLT = 147 :
Take pleasure in!
Construct
Winshark is driven by cmake:
git clone https://github.com/airbus-cert/winshark --recursive
mkdir construct_winshark
cd make_winshark
cmake ..Winshark
cmake --establish . --target bundle --config launch
How does it get the job done
To better fully grasp how Winshark operates, we have to have to recognize how ETW performs very first.
ETW is break up into 3 areas:
- A Service provider that will emit log and determined by a unique ID
- A Session that will combine 1 or additional companies
- A Purchaser that will examine logs emitted by a session
Supplier
There is a lot of various sorts of suppliers. The most common, and usable, are registered companies. A registered company, or a manifest-primarily based service provider, is recorded underneath the registry crucial HKLMSOFTWAREMicrosoftWindowsCurrentVersionWINEVTPublishers. This makes the connection concerning a company ID and a dll. The manifest is encompassed into the connected dll into a source name WEVT_TEMPLATE.
You can list all vendors registered on your equipment applying logman:
logman query companies
You can also checklist all companies sure by a unique procedure:
logman question companies -pid 1234
Some of them could show up without having a title these sorts of providers can deliver WPP or TraceLogging logs.
Session
Classes are established to gather logs from additional than a person service provider. You can create your personal session utilizing logman:
logman get started Mysession -p "Microsoft-Windows-RemoteDesktopServices-RdpCoreTS" -ets -rt
logman update MySession -p "Microsoft-Windows-NDIS-PacketCapture" -ets -rt
You can checklist all energetic classes from an admin command line:
logman query -ets
Knowledge Collector Set Sort Standing
-------------------------------------------------------------------------------
...
EventLog-Software Trace Jogging
EventLog-Microsoft-Windows-Sysmon-Operational Trace Functioning
EventLog-Method Trace Working
...
The command done efficiently.
You can see in this article some fascinating periods use by the function logger to seize logs from Software and Technique classes and from Sysmon.
Buyer
A customer is a straightforward plan that will browse logs from a session. Nicely-recognised shoppers are:
- Event Logger
logmannetshtracert
And now Winshark!!! Winshark is a simple ETW client. The serious underlying shopper is libpcap, (wpcap.dll for Windows) which is employed by dumpcap.exe which is the course of action in demand of packet capture.
Wireshark
Wireshark is split into a few areas (of course, him much too):
Wireshark.exewhich is in cost of parsing and dissecting protocolsdumpcap.exewhich is in demand of capturing packetslibpcap(wpcap.dll) which is in charge of interfacing concerningdumpcap.exeand the Working Technique
Winshark takes area in the very first and previous sections. It implements a backend for libpcap to capture ETW events.Winshark operates on ETW sessions, this is why you can choose an ETW session in location of the Community interface at the start off of seize. Then Winshark generates lua dissectors for every single manifest-dependent supplier registered on your personal computer, through the installation stage. Winshark is also capable to parse trace logging-primarily based vendors.
Seize community visitors
To seize community website traffic using Winshark, you have to simply just activate network tracing via netsh:
netsh.exe trace get started capture=of course report=no correlation=no
And then create an ETW session associated with the Microsoft-Home windows-NDIS-PacketCapture provider:
logman start off Winshark-PacketCapture -p "Microsoft-Home windows-NDIS-PacketCapture" -rt -ets
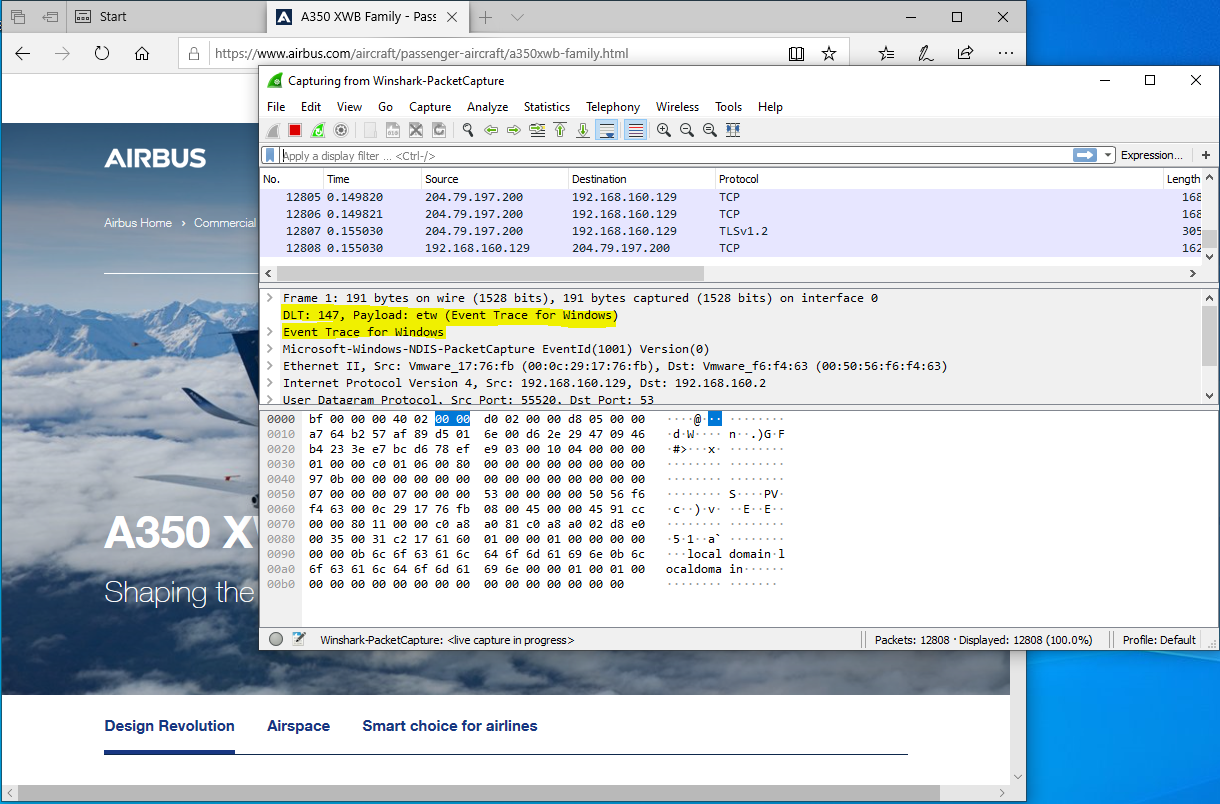
Then launch Wireshark with administrator privileges and pick the Winshark-PacketCapture interface:
That will start off the packet capture:
Filtering on the system ID
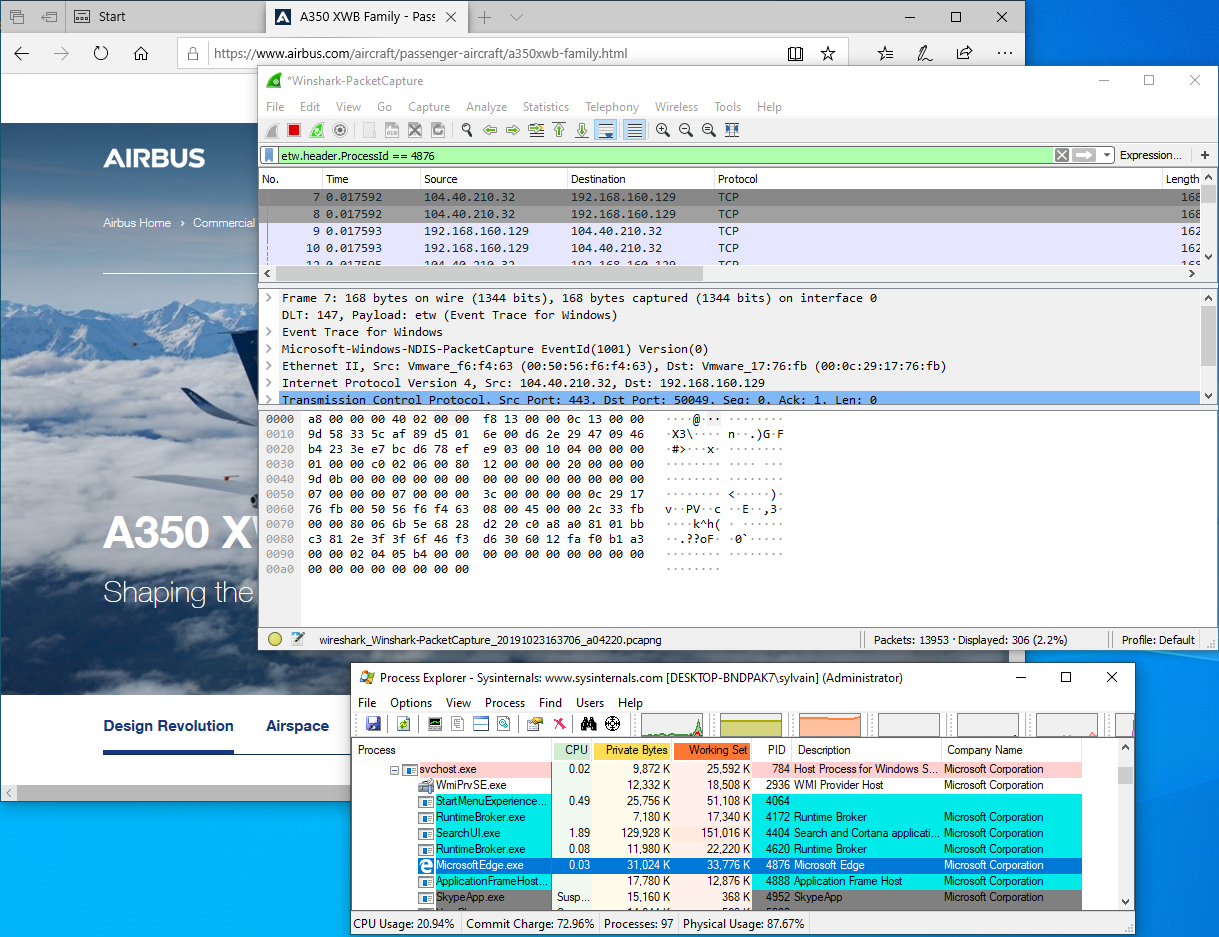
ETW marks each packet with a header that sets some metadata about the sender. Just one of these is the System IDof the emitter. This is a huge enhancement from a common packet capture from an NDIS driver. Simply fill the filter area of Wireshark with the following expression:
etw.header.ProcessId == 1234
Capturing NamedPipe
@kobykahane provides a file procedure filter driver that emits an ETW for every motion executed on a NamedPipe.
Put in
- Move driver signing check in test manner
bcdedit /set testsigning on
- Put in NpEtwSetup.msi
- Reboot
- Update
Winsharkdissector by double-clickingC:Application FilesWiresharkWinsharkUpdate.batwithAdminrights
Seize
- Open a
cmd.exeinAdmin method - Begin the driver
sc begin NpEtw
- Make an ETW Session
logman get started namedpipe -p NpEtw -ets -rt
- Start
Wiresharkand select thenamedpipesession. Enjoy!
SSTIC (Symposium sur la sécurité des systems de l’information et des communications)
This project is component of a presentation created for SSTIC
https://github.com/airbus-cert/Winshark
The put up Winshark – Wireshark plugin to work with Function Tracing for Windows appeared 1st on Hakin9 – IT Stability Magazine.