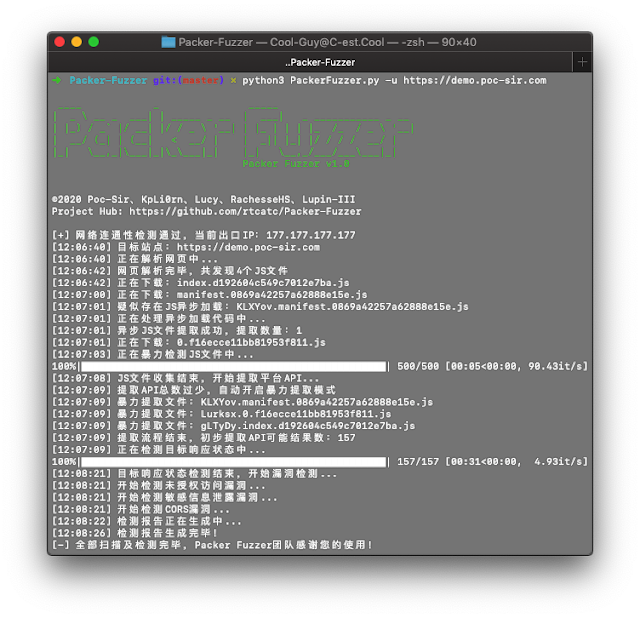
Packer-Fuzzer – A Fast And Efficient Scanner For Security Detection Of Websites Constructed By Javascript Module Bundler Such As Webpack

With the reputation of net entrance-conclusion packaging resources, have you encountered a lot more and more internet sites represented by Webpack packager in day-to-day penetration tests and stability expert services? This sort of packager will deal the API and API parameters of the overall website together for centralized World wide web contact, which is also handy for us to speedily explore the capabilities and API lists of the site, but often the variety of JS information generated by these packagers is unusually large and complete The amount of money of JS code is really large (much more than ten thousand lines), which provides fantastic inconvenience to our manual screening, and the Packer Fuzzer software arrived into becoming.
This software supports computerized fuzzy extraction of the API corresponding to the focus on web-site and the parameter articles corresponding to the API, and supports the fuzzing and efficient fuzzing of seven vulnerabilities: unauthorized obtain, delicate information leakage, CORS, SQL injection, unauthorized obtain, weak password, and arbitrary file add Quick detection. After the scan is above, this resource also supports computerized technology of scan reviews. You can pick the HTML version that is straightforward to analyze and the far more formal doc, pdf, txt versions.
And you really do not have to fear about language challenges brought on by internationalization. This tool comes with 5 big language deals (together with report templates): Simplified Chinese, French, Spanish, English, and Japanese (sorted according to translation precision). NoProfessional team translation.
Parameter introduction
You can use the python3 PackerFuzzer.py [options] command to operate this tool. The written content of alternatives is as follows:
–h (–support)
Assist command, no supplemental parameters, see all the parameters supported by this resource and their corresponding introduction
–u (–url)
The URL path of the web site to be scanned is a needed selection, for example: -u https://demo.poc-sir.com
–c (–cookie)
Further cookies articles, can be vacant, if stuffed in, it will be passed globally, for illustration: -c “POC=666SIR=233”
–d (–head)
More HTTP header information, which can be vacant, if loaded in, it will be passed in globally, the default is Cache-Control:no-cache, for case in point: -d “Token:3VHJ32HF0”
–l (–lang)
Language choice, when it is empty, the process will mechanically pick out the corresponding language choice, if there is no corresponding language pack, it will instantly switch to the English interface. The available language packs are: Simplified Chinese (zh), French (fr), Spanish (es), English (en), Japanese (ja), for illustration: -l zh
–t (–type)
It is divided into primary variation and innovative edition. When it is vacant, the essential version is utilized by default. The superior variation will rescan all APIs and fuzzy extract the corresponding parameters of the API, and execute: SQL injection vulnerabilities, horizontal unauthorized vulnerabilities, weak password vulnerabilities, and arbitrary file add vulnerabilities. You can use the adv solution to enter the superior version, for illustration: -t adv
–p (–proxy)
Global proxy, can be vacant, if you fill in, use proxy IP globally, for instance: -p https://hack.cool:8080
–j (–js)
Added JS file, can be empty, when you imagine there are other JS documents that need to have to be analyzed by this device, you can use this solution, for illustration: -j https://demo.poc-sir.com/js/index.js, https://demo.poc-sir.com/js/vue.js
–b (–foundation)
Specify the center element of the API (for case in point, when an API is: https://demo.poc-sir.com/v1_api/login, its basedir is: v1_api), it can be vacant, when you think the immediately extracted basedir of this resource is not correct , You can use this option, for instance: -b v1_api
–r (–report)
Specify the report structure to be generated. When it is empty, HTML and DOC format stories are created by default. Obtainable report formats are: html, doc, pdf, txt, for illustration: -r html,pdf
–e (–ext)
Whether to enable the extension plug-in alternative, this resource supports users to self-produce plug-ins and save them in the ext directory (for how to generate, remember to refer to the demo.py file in the corresponding directory). The default is off. When the person employs the on command to open, the tool will automatically execute the plug-ins in the corresponding listing, for case in point: -e on
–f (–flag)
The SSL connection stability solution, when it is empty, is shut by default. In this state, all insecure connections will be blocked. If you want to ignore the SSL security standing, you can use the 1 command to help it, and all certificate problems will be dismissed, for case in point: -f 1
-s (–silent)
The Silent option, the moment enabled, all operations that ask for Indeed or NO will quickly be established to Indeed, and the content material right after the parameter is the name of the scan report (customized report name), which can be utilised for unattended, batch operations, plug-in phone calls, for illustration: -s Scan_Undertaking_777.