CRLFMap – A Tool To Find HTTP Splitting Vulnerabilities

CRLFMap is a device to obtain HTTP Splitting vulnerabilities
Why?
- I wished to compose a tool in Golang for concurrency
- I wanted to be ready to fuzz each parameters and paths
Set up
go get github.com/ryandamour/crlfmapEnable
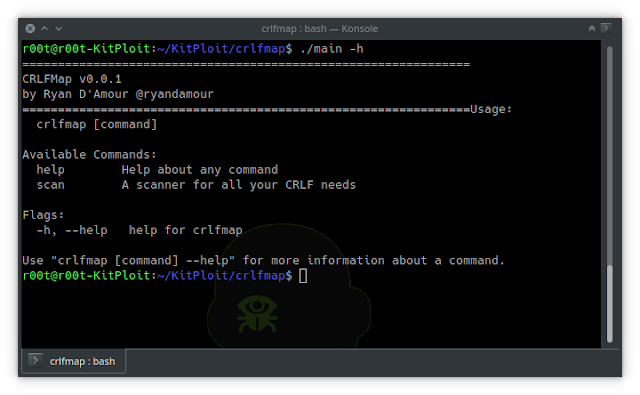
Readily available Commands:
support Help about any command
scan A scanner for all your CRLF requires
Flags:
-h, --enable help for crlfmapscan use
crlfmap scan --domains domains.txt --output outcomes.txt
===============================================================
CRLFMap v0..1
by Ryan D'Amour @ryandamour
===============================================================
_ __
| |/ _|
___ _ __| | |_ _ __ ___ __ _ _ __
/ __| '__| | _| '_ ' _ / _' | '_
| (__| | | | | | | | | | | (_| | |_) |
___|_| |_|_| |_| |_| |_|__,_| .__/
| |
|_|
v0..1
-----------------------
:: Domains : domains.txt
:: Payloads : payloads.txt
:: Threads : 1
:: Output : results.txt
:: User Agent : Mozilla/5. (X11 Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chr ome/81..4044.138 Safari/537.36
:: Timeout : 10
:: Delay :
-----------------------
[+]http://localhost:3000/v1/%0AInjected-Header:CRLFInjecttest.json: is Susceptible
[+]http://localhost:3000/v1/%20%0AInjected-Header:CRLFInjecttest.json: is VulnerableContributing
Pull requests are welcome. For big alterations, you should open an issue to start with to explore what you would like to adjust.
Please make guaranteed to update assessments as suitable.