North Korean APT Group ‘Kimsuky’ Hack Techniques and Method

The North Korean advanced persistent threat (APT) group known as Kimsuky is actively attacking commercial-sector businesses, often by posing as South Korean reporters, according to an alert from the U.S. Cybersecurity and Infrastructure Security Agency (CISA). The Department of Homeland Security CISA this week issued an Alert (AA20-301A) titled North Korean Advanced Persistent Threat Focus: Kimsuky warning U.S. businesses, and particularly those in the commercial sector, about tactics used by APT group Kimusky.
Kimsuky (known as Hidden Cobra) has been operating as a cyberespionage group since 2012 under the auspices of the regime in Pyongyang. Its mission is global intelligence gathering, CISA noted, which usually starts with spear phishing emails, watering-hole attacks, torrent shares and malicious browser extensions, in order to gain an initial foothold in target networks, These terminologies are explained in Social Engineering – The Art of Hacking. Primary targets include diplomatic and high-level organizations in Japan, South Korea and the United States, with a focus on foreign policy and national-security issues related to the Korean peninsula, nuclear policy and sanctions, CISA added. It also targets the cryptocurrency industry. CISA, FBI, and CNMF recommended targeted individuals and organizations to increase their defenses and adopt a heightened state of awareness. Particularly important mitigations include safeguards against spear phishing, use of multi-factor authentication, and user awareness training.
APT Hack Tactics
Initial Acess
- By using different spear phishing methods, Kmisky gained initial access to the victim’s networks. Spear phishing is the most commonly noticed and well known tactic used by Kimsuky.
- APT stole credentials from victims that were not their usual targets and used them to host their contagious scripts and tools. It’s most likely these credentials were obtained using spear phishing and credentials harvesting scripts.
- Subdomains were created copying the victim domains. To gain trust, emails were also sent by Kimsuky containing malicious links. Pretending to be South Korean reporters, many interview type emails were sent to build rapport.
- The targets were then invited to skype interviews to discuss Korean issues. After the victim agreed on giving the interview, a malware was sent as an attachment of sorts and then later on cancelled the interview.
- Kimsuky cleverly approaches the targets to discuss topics that are relevant to them. Some other methods include login-security-alert-themed phishing emails, watering hole attacks, distributing malware through torrent sharing sites, and directing victims to install malicious browser extensions.
Implementation
After getting the initial access, Kimsuky most likely uses the Babyshark malware or the command shell to execute, Babyshark malware is Visual Basic Script (VBS) based malware. The breakdown is as follows:
- First, the compromised host system uses the native Microsoft Windows utility, mshta.exe, to download and execute an HTML application file from a remote system
- The HTA file then downloads, decodes, and executes the encoded BabyShark VBS file.
- The script maintains Persistence by creating a Registry key that runs on startup.
- It then collects system information, sends it to the operator’s command control servers, and awaits further commands.
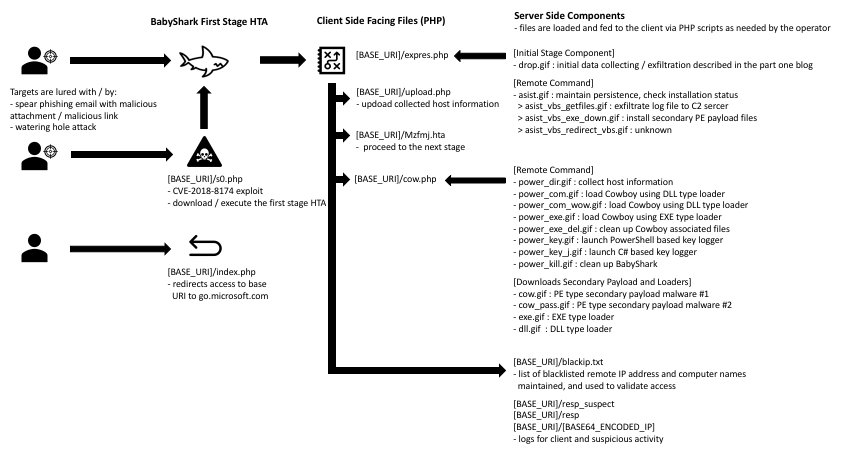
It has been indicated by open-source reporting that Babyshark is delivered via an email message containing a link or an attachment. Kimsuky tailors email phishing messages to match its targets’ interests. Without even having to touch the physical computer hard disk, Kimsuky uses PowerShell to run executables from the internet by using the target’s memory. PowerShell scripts can be executed without invoking powershell.exe through HTA files or mshta.exe.
Persistence
Kimsuky has demonstrated the ability to establish Persistence through using malicious browser extensions, modifying system processes, manipulating the autostart execution, using Remote Desktop Protocol (RDP), and changing the default file association for an application. By using these methods, Kimsuky a.k.a Hidden Cobra can gain login and password information and/or launch malware outside of some applications that allow listing solutions.
Sometime in 2018, Kimsuky used an extension on Google Chrome Web Store, to infect victims and steal passwords and cookies from their browsers. The extension had a five-star rating, however after reading the text of the reviews these reviews were most likely left by Google+ accounts that had been compromised.
By mimicking a related operating system function or even by disguising as a software, Kimsuky might install a new service that can run at startup by using utilities to interact with services or by directly modifying the Registry keys.
During the Stolen Pencil operation in May 2018, Kimsuky used the Grease malware. A tool that can add a Windows administrator account and enable RDP while avoiding the rules of firewall. Kimsuky also uses a document stealer module that changes the default program associated with Hangul Word Processor (HWP, a Korean word processor) documents in the Registry. The default Registry setting is manipulated by Kimsuky to open a malicious program instead of the original HWP program. Before the real HWP program opens the document, malware will read and email the content from HWP documents. This method makes the Microsoft Office users also a target.
Kimsuky maintains access to compromised domains by uploading actor-modified versions of open-source Hypertext Processor (PHP)-based web shells; which enables the APT actor to upload, download, and delete files and directories on the compromised domains.
Privilege Escalation
Privilege escalation is the act of exploiting a bug, design flaw or configuration oversight in an operating system or software application to gain elevated access to resources that are normally protected from an application or user. Well-known methods for Privilege Escalation are used by Kimsuky, including placing scripts in the Startup folder, creating and running new services, changing default file associations, and injecting malicious code in explorer.exe. Following methods were primarily used
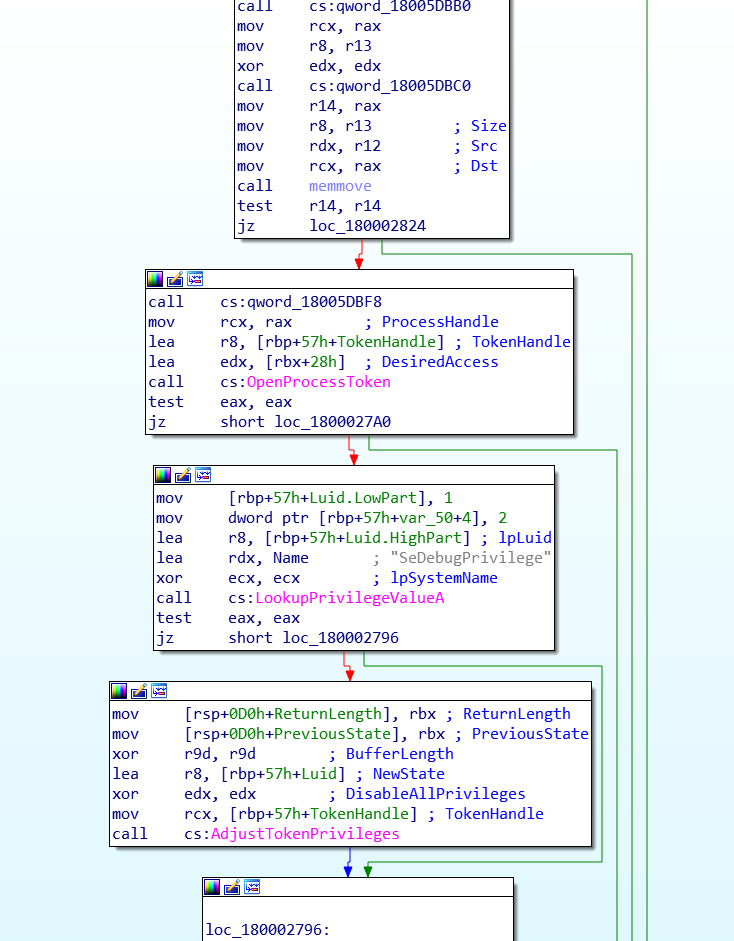
- Kimsuky has used Win7Elevate—an exploit from the Metasploit framework—to bypass the User Account Control to inject malicious code into explorer.exe. Irrespective of what operating system the victim is using, this malicious code decrypts its spying library from resources. It then saves the decrypted file to a disk with a random but hardcoded name in the user’s temporary folder and loads this file as a library, ensuring the tools are then on the system even after a reboot. Escalation of privileges is thus allowed by this process.
- Before the injection takes place, the malware sets the necessary privileges. The malware writes the path to its malicious Dynamic Link Library (DLL) and ensures the remote process is loaded by creating a remote thread within explorer.exe.
Evasion Mechanism
Kimsuky uses well-known and widely available methods for Defense Evasion within a network. Defense Evasion consists of techniques that malware use to avoid detection throughout their compromise. These methods include disabling security tools, deleting files, and using Metasploit.
- Kimsuky’s malicious DLL runs at startup to turn off the Windows firewall Registry keys. This disables the Windows system firewall and turns off the Windows Security Center service, preventing the service from alerting the user about the disabled firewall
- Kimsuky uses a keylogger that deletes exfiltrated data on disk after it is transmitted to its C2 server
- Kimsuky has used mshta.exe, which is a utility that executes Microsoft HTAs. It can be used for proxy execution of malicious .hta files and JavaScript or VBS through a trusted windows utility.
- Win7Elevate is also used to evade traditional security measures, which has been mentioned above.
SYSTEMCurrentControlSetServicesSharedAccessParameters
FirewallPolicyStandardProfile
EnableFirewall = 0
SYSTEMCurrentControlSetServicesSharedAccessParameters
FirewallPolicyPublicProfile
EnableFirewall = 0
HKLMSOFTWAREAhnLabV3IS2007InternetSec
FWRunMode = 0
HKLMSOFTWAREAhnlabV3IS80is
fwmode = 0Credential Access
Credential Access consists of techniques for stealing credentials like account names and passwords. Kimsuky uses legitimate tools and network sniffers to harvest credentials from web browsers, files, and keyloggers. Kimsuky gains credential access in the following manner
- Kimsuky uses memory dump programs instead of using well-known malicious software and performs the credential extraction offline.
- Kimsuky then uses ProcDump, a Windows command line administration tool, that allows a user to create crash dumps/core dumps of processes based upon certain criteria, such as CPU utilization.
- ProcDump monitors for CPU spikes and generates a crash dump when a value is met; it passes information to a Word document saved on the computer. It can be used as a general process dump utility that actors can embed in other scripts, as seen by Kimsuky’s inclusion of ProcDump in the BabyShark malware.
Kimsuky abuses a Chrome extension to steal passwords and cookies from browsers, as per open-source security researchers. The initial email directs a victim to a phishing site, where the victim is shown a PDF document but is not able to view it. The victim is then redirected to the official Chrome Web Store page to install a Chrome extension, which has the ability to steal cookies and site passwords and loads a JavaScript file, named jQuery.js, from a separate site.
Kimsuky also uses a PowerShell based keylogger, Mechanical, and a network sniffing tool, named Nirsoft SniffPass. Mechanical logs keystrokes to %userprofile%appdataroamingapach.txt,log and is also a “cryptojacker,” which is a tool that uses uses the computer’s resources to mine forms of online money known as cryptocurrencies. Nirsoft SniffPass is capable of obtaining passwords sent over non-secure protocols. Kimsuky used actor-modified versions of PHProxy, a PHP written open source web proxy, for the purpose of examining web traffic between the victim and the website accessed by the victims and to collect any credentials entered by the victim.
Discovery / Scan
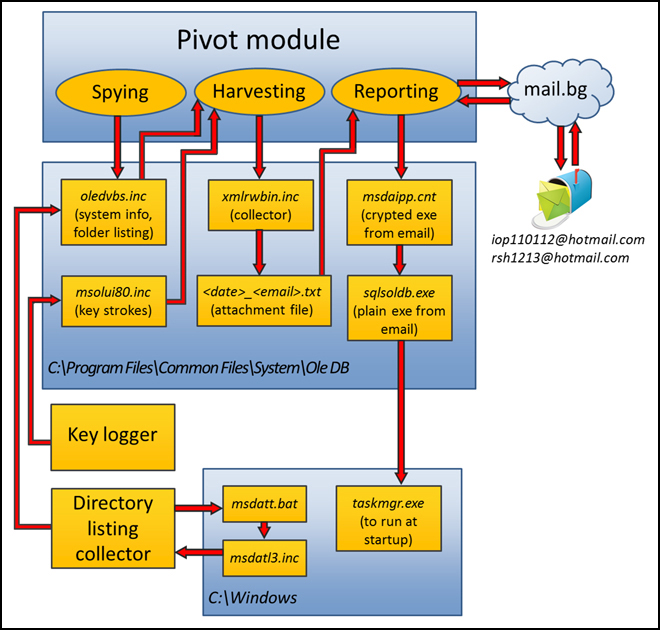
Kimsuky identifies system information and the file structure for victims’ computers and networks. Discovery consists of techniques an adversary may use to gain knowledge about the system and internal network. Kimsuky seems to be relying on using the victim’s computer’s command prompt to identify the file structure and system information. The information is directed to C:WINDOWSmsdatl3.inc, read by malware, and then most likely emailed to the malware’s command and control server.
Data & Info Collection
Through its HWP document malware and its keylogger, Kimsuky collects data from the victim’s system. The HWP document malware changes the default program association in the Registry to open HWP documents. As soon as the user opens a HWP file, the Registry key change activates the malware that opens the HWP document and then sends a copy of the HWP document to an account under the adversary’s control. Then the malware allows the file to be opened in a normal way without being detected. The keylogger intercepts keystrokes and writes them to C:Program FilesCommon FilesSystemOle DBmsolui80.inc and records the active window name where the user pressed keys.
A Python implant that gathers data from Mac OS systems and sends it to a C2 server was also used by Kimsuky.
Command and Control Mechanism
A modified TeamViewer client is used (version 5.0.9104) for Command and Control.
- During the initial infection, the service “Remote Access Service” is created and adjusted to execute C:WindowsSystem32vcmon.exe at system startup. Every time vcmon.exe is executed, it disables the firewall by turning off registry values.
- The program then modifies the TeamViewer Registry settings by changing the TeamViewer strings in TeamViewer components.
- The launcher then configures several Registry values, including SecurityPasswordAES, that control how the remote access tool will work. The SecurityPasswordAES Registry value represents a hash of the password used by a remote user to connect to TeamViewer Client. This way, the attackers set a pre-shared authentication value to have access to the TeamViewer Client. The attacker will then execute the TeamViewer client netsvcs.exe.
Exfiltration Procedures
Two different methods have been described by open sources that Kimsuky has used to exfiltrate stolen data: email or through an RC4 key generated as an MD5 hash or a randomly generated 117-bytes buffer. Data exfiltration occurs when malware and/or a malicious actor carries out an unauthorized data transfer from a computer
During data exfiltration, no indications were shown that would suggest that the actor destroyed computers during the observed exfiltration’s, suggesting Kimsuky’s intention is to steal information, not to disrupt computer networks. Kimsuky’s preferred method for sending or receiving exfiltrated information is through email.
Kimsuky also uses an RC4 key generated as an MD5 hash or a randomly generated 117-bytes buffer to exfiltrate stolen data. The data is sent RSA-encrypted. Kimsuky’s malware constructs an 1120-bit public key and uses it to encrypt the 117-bytes buffer. The resulting data file is saved in C:Program FilesCommon FilesSystemOle DB.
Identify Kimsuky Compromised Machines
Kimsuky has used the domains listed in following table to carry out its objectives:
Domains Used
| login.bignaver[.]com | nytimes.onekma[.]com | webuserinfo[.]com |
| member.navier.pe[.]hu | nid.naver.onektx[.]com | pro-navor[.]com |
| cloudnaver[.]com | read.tongilmoney[.]com | naver[.]pw |
| resetprofile[.]com | nid.naver.unicrefia[.]com | daurn[.]org |
| servicenidnaver[.]com | mail.unifsc[[.]com | naver.com[.]de |
| account.daurn.pe[.]hu | member.daum.unikortv[.]com | ns.onekorea[.]me |
| login.daum.unikortv[.]com | securetymail[.]com | riaver[.]site |
| account.daum.unikortv[.]com | help-navers[.]com | mailsnaver[.]com |
| daum.unikortv[.]com | beyondparallel.sslport[.]work | cloudmail[.]cloud |
| member.daum.uniex[.]kr | comment.poulsen[.]work | helpnaver[.]com |
| jonga[.]ml | impression.poulsen[.]work | view-naver[.]com |
| myaccounts.gmail.kr-infos[.]com | statement.poulsen[.]work | view-hanmail[.]net |
| naver.hol[.]es | demand.poulsen[.]work | login.daum.net-accounts[.]info |
| dept-dr.lab.hol[.]es | sankei.sslport[.]work | read-hanmail[.]net |
| Daurn.pe[.]hu | sts.desk-top[.]work | net.tm[.]ro |
| Bigfile.pe[.]hu | hogy.desk-top[.]work | daum.net[.]pl |
| Cdaum.pe[.]hu | kooo[.]gq | usernaver[.]com |
| eastsea.or[.]kr | tiosuaking[.]com | naver.com[.]ec |
| myaccount.nkaac[.]net | help.unikoreas[.]kr | naver.com[.]mx |
| naver.koreagov[.]com | resultview[.]com | naver.com[.]se |
| naver.onegov[.]com | account.daum.unikftc[.]kr | naver.com[.]cm |
| member-authorize[.]com | ww-naver[.]com | nid.naver.com[.]se |
| naver.unibok[.]kr | vilene.desk-top[.]work | csnaver[.]com |
| nid.naver.unibok[.]kr | amberalexander.ghtdev[.]com | nidnaver[.]email |
| read-naver[.]com | nidnaver[.]net | cooper[.]center |
| dubai-1[.]com | coinone.co[.]in | nidlogin.naver.corper[.]be |
| amberalexander.ghtdev[.]com | naver.com[.]pl | nid.naver.corper[.]be |
| gloole[.]net | naver[.]cx | naverdns[.]co |
| smtper[.]org | smtper[.]cz | naver.co[.]in |
| login.daum.kcrct[.]ml | myetherwallet.com[.]mx | downloadman06[.]com |
| login.outlook.kcrct[.]ml | myetherwallet.co[.]in | loadmanager07[.]com |
| top.naver.onekda[.]com | com-download[.]work | com-option[.]work |
| com-sslnet[.]work | com-vps[.]work | com-ssl[.]work |
| desk-top[.]work | intemet[.]work | jp-ssl[.]work |
| org-vip[.]work | sslport[.]work | sslserver[.]work |
| ssltop[.]work | taplist[.]work | vpstop[.]work |
| webmain[.]work | preview.manage.org-view[.]work | intranet.ohchr.account-protect[.]work |
Redacted domains
| [REDACTED]/home/dwn[.]php?van=101 | [REDACTED]/home/dwn[.]php?v%20an=101 | [REDACTED]/home/dwn[.]php?van=102 |
| [REDACTED]/home/up[.]php?id=NQDPDE | [REDACTED]/test/Update[.]php?wShell=201 |
Conclusion
Malware name and coding keep changing but the attack pattern is generally same as seen by so many malwares / ransomware in recent years. Hacking of networks and personal machines will not stop but one need to learn how to identify such hacking attempts and stay clear.
The post North Korean APT Group ‘Kimsuky’ Hack Techniques and Method first appeared on Internet Security Blog – Hackology.



